Welcome to the Phish Market!
Our Phish Market is a selection of phishing attempts made on members of the KSU community. We have collected them here for you to peruse so that you are familiar with their
foul smell when they hit your inbox.
What is phishing?
Phishing is the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
If you have mistakenly provided credentials to a confirmed phishing email, please change your NetID password immediately at netid.kennesaw.edu. If you receive a suspicious email not currently in the Phish Market, please forward it to abuse@kennesaw.edu.
Spot the threat!
Email is the official method of communication at KSU; all announcements and business-related correspondence are shared by official KSU email accounts. Please follow the reporting instructions above if you receive suspicious emails. To prevent hacks, incorporate the following tips as part of your email checking routine.
Tips for assessing an email
-
Look for [EXTERNAL] in the email subject line.
This indicates that the email may come from a non-KSU sender. Check to see if the email address ends in "@kennesaw.edu." If not, the email may be a phishing attempt.
-
Don’t automatically trust an email sender's display name.Even if the name displayed matches the name of a person you know, check the email address to confirm the sender. Any email claiming to be an employee of the university that does not originate from email ending in “@kennesaw.edu” should be held in suspicion, especially if it claims to be from a person of leadership.
-
Check (but do not click) the links to web sites.Hover your cursor over any links in the message and note the address. Does the address make sense and match the rest of the content of the email? For example, links to most KSU or USG sites will include kennesaw.edu or usg.edu. The same is typically true of other companies.
-
Check for errors.Attackers are often less careful about spelling or grammar than legitimate senders.
-
Be cautious about attachments.Do not click on attachments that are unexpected or from unknown senders.
-
Beware of urgency.Remember that scammers might try to make it sound as if there is an emergency (e.g., someone needs money right away, your account has been compromised, or someone is in trouble). If the sender is trying to influence you to act quickly, it may be wise to slow down instead.
-
Take time to think it through.Phishers can use company logos, photos, and even spoof email addresses to make their attempts look more legitimate. Take extra caution in reviewing an email that you did not expect to receive and asks you to take action
Report Phishing at KSU
If you have any doubts about the legitimacy of an email, report it to University Information Technology Services (UITS)! Forward it to abuse@kennesaw.edu, or click the "Phish Alert Report" button in Outlook.
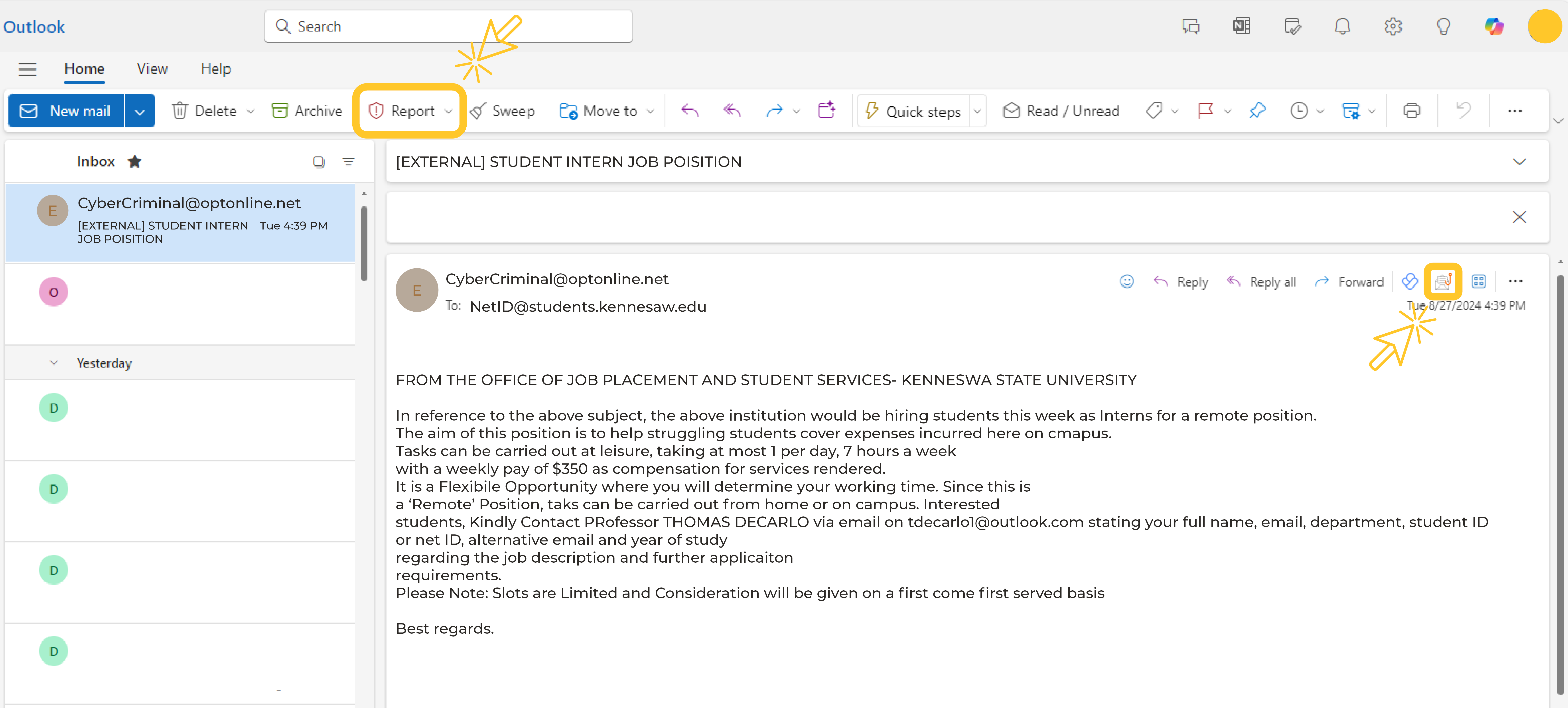
The Phish Alert Report button can look slightly different based on whether you're using Outlook on the Web, the Outlook app on your computer, or Outlook for mobile devices.
Phish Alert Report Button in Outlook
Phish Alert Report Button on iOS and Android
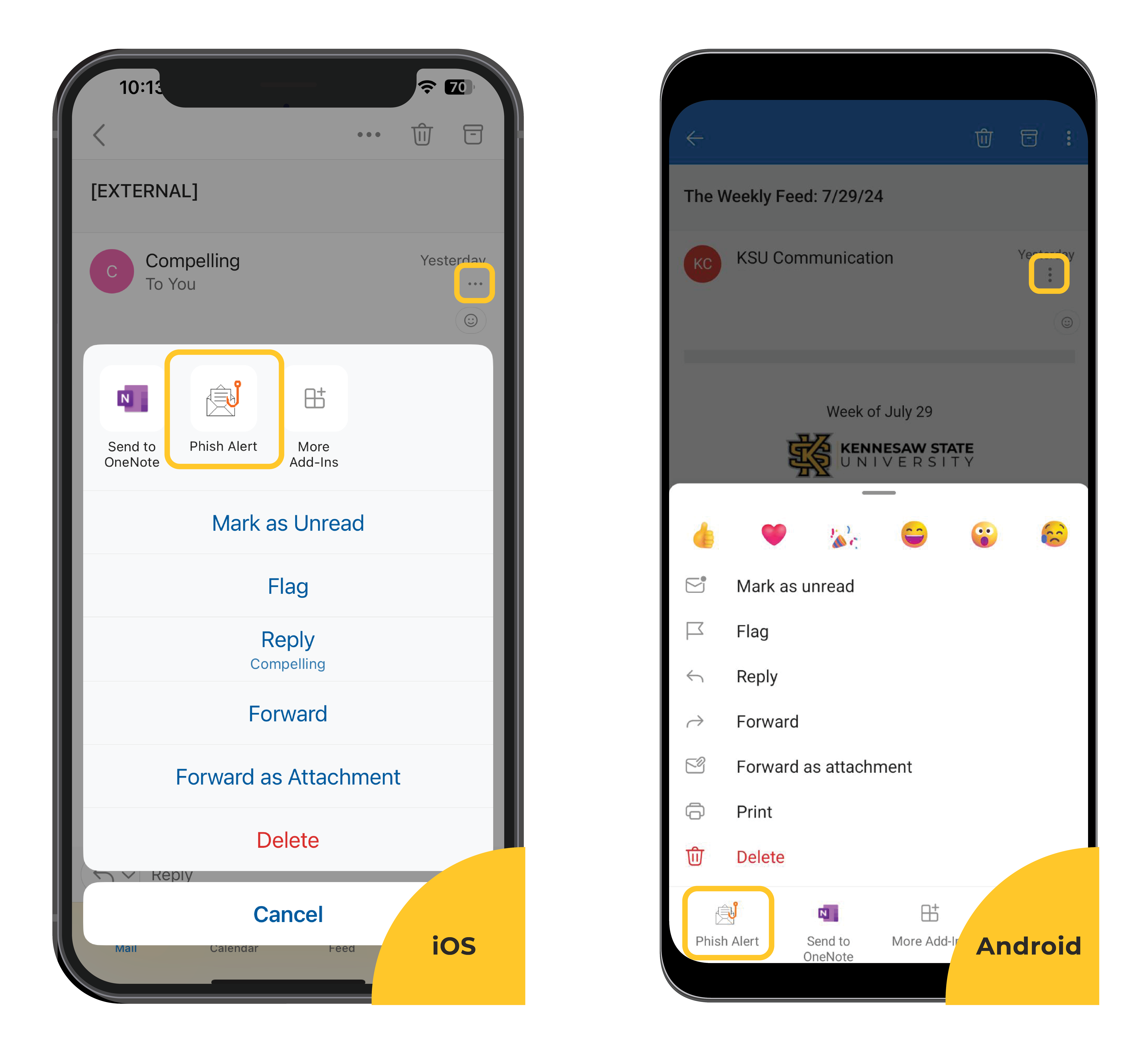
-
What happens when I click the Phish Alert Button?
When you click the "Phish Alert Report" button, another pop-up on the right-hand side of the screen will confirm your choice to report the email. The email will then be deleted from your inbox and forwarded to the UITS Office of Cybersecurity for investigation.
-
What happens if I made a mistake clicking the Phish Alert Button and need to access an email?
If you need to access a message that has been reported, you can find it in the "Deleted Items" folder (until it has been emptied, which makes the deletion permanent). As long as the message is still in the "Deleted Items" folder, it can be moved back to your inbox.
-
What if I'm not sure whether or not an email is a phishing attempt?
It's always better to err on the side of caution. If you are unable to verify a sender's unusual or suspicious request in-person, by phone, or through a Teams message, you can report that message by clicking the "Phish Alert Report" and confirming your submission on the pop-up panel on the right-hand side of the screen. You can also check the Phish Market site for information about any ongoing, campus-wide alerts.
Examples of real phishing emails at KSU
















